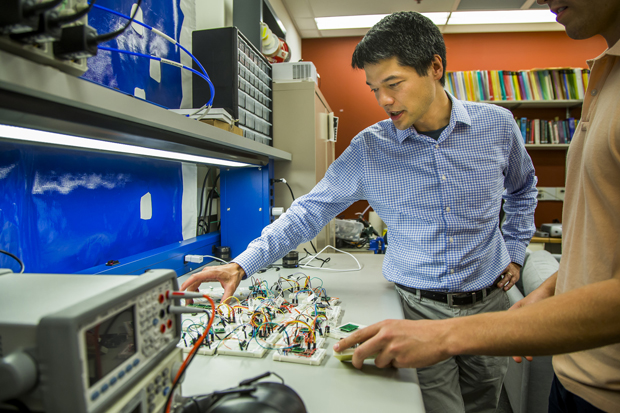
Above: Kevin Fu (front right) and his research group are testing the security and privacy of various medical devices, including heart-rate sensors, pacemakers, defibrillators, drug-delivery systems, and neurostimulators. (Photo courtesy of Joseph Xu, University of Michigan College of Engineering.)
Every device that contains a computer component is open to cyberattacks, and that potential escalates when the device is connected to another device, an information technology (IT) network, or the Internet. This is especially troublesome when it comes to medical devices, because patient care hangs in the balance.
What do developers need to know about possible threats to their medical devices, and how they can keep their devices out of harm’s way? To find out, IEEE Pulse interviewed three cybersecurity experts: Anura S. Fernando, Kevin Fu, and George Gray.
Fernando is principal engineer with the Medical Software and Systems Interoperability Health Sciences Division at the global science-safety organization Underwriters Laboratories (UL), which has developed cybersecurity standards for devices across industries. He has also served as a member of both the U.S. Food and Drug Administration (FDA) Safety and Innovation Act working group and the Health Care Industry Cybersecurity Task Force.
Fu, Ph.D., is an associate professor of electrical engineering and computer science at the University of Michigan and chief scientist with Virta Labs of Seattle, Washington, which provides hospitals with safety-conscious cybersecurity software to manage risks in clinical networks [1].
Gray is chief technology officer and vice president of software development at Ivenix of North Andover, Massachusetts, which is developing an innovative infusion system to streamline medication delivery and bring legacy technology into the digital age [2].
IEEE Pulse: What are the big cybersecurity threats out there today, in terms of the healthcare industry and for medical devices?

Anura S. Fernando: I think there are a number of different threats. People tend to think of a sick person connected to a medical device and somebody who hacks into that device to cause harm to that individual. While that’s certainly a viable scenario, it’s not all that common. What is much more prevalent are threats driven by organized crime for financial assets. There’s personally identifiable information, such as Social Security numbers, in hospital systems that are significant targets; and there’s insurance information that can be used for insurance fraud. There’s also industrial espionage for the purpose of intellectual property theft. If you think about medical devices, the hardware is becoming almost a secondary asset, and it’s really the algorithms that are of significant value, so, if you can acquire that through hacking the devices and stealing the IT, it’s a pretty simple matter to replicate the hardware and flood the market with copies of products.
There is also a threat from terrorist activity. If you look at some of the recent ransomware attacks, you can see that hospitals can be quite debilitated by ransomware, or any malware for that matter, because it can affect procedures. In some cases, a hospital might have to stop providing health care to patients and actually transport them to different facilities. So let’s say a terrorist pursues a coordinated attack, maybe setting off a bomb in a populated area and then debilitating the healthcare infrastructure in that area. That can have various consequences from a national security perspective.
Beyond those threats, there is also the potential for malicious mischief that involves things like tampering with clinical trials. We tend to think of individual patients being harmed, but if you tamper with a clinical trial, you can have a whole population of patients who have waited for a new drug or a new medical device to come out—potentially to save their lives—and now have that trial set back. That might result in a generation of fatalities.

Kevin Fu: The media play up the risk of the wily hacker, and there is some truth to that, but I think this particular risk is really overplayed. At the end of the day, what we want is safer, more effective medical devices for better patient outcomes, and it’s very difficult to get safety without security. To me, the threat is really about integrity and the availability of medical devices to deliver patient care, and some of these devices are so insecure that it’s like breaking down an open door. It doesn’t really take much skill; it’s fairly easy to cause harm; and that’s why I’m concerned about the integrity and the availability.
IEEE Pulse: How are medical devices vulnerable to cybersecurity attacks?
Fu: Ransomware is the risk du jour affecting the availability of patient care, and this may not be somebody targeting you but instead targeting easy prey: the hospitals. Hospitals are more exposed to these kinds of risks because they tend to use very old software and to have complicated systems that can be hard to maintain and, therefore, allow ransomware to get in. Once that happens, it can affect things like chart data and medical records, and, because things are so interconnected, it can affect your device.
I’m also particularly concerned with the integrity of medical information as well as diagnostics and therapeutics. For example, imagine that a computer virus breaks into a medical device and then flips a bit on HIV test results. The damage is to the integrity. What do you think the hospital is going to do—redo all of the tests? Another example is hackers who make a ransom claim that they have adulterated one database in a hospital’s cancer tests, but they won’t say which one until a ransom is paid. We haven’t seen an imminent threat like that at the moment, but it’s clear that this could change tomorrow.

George Gray: Sometimes hackers go after you because you’re delivering therapy and they want to disrupt that; but, other times, it’s because they want to use you as an attack vector. For instance, [the department store chain] Target had a large breach [in which] a number of credit cards were exposed, and the way that [the hackers] broke in was through their HVAC [heating, ventilation, and air conditioning] system [3]. Once they got in, the HVAC system was trusted by another system, which was trusted by another system, and that eventually led to the credit card numbers.
Likewise, a lot of developers think, “I’m just making a pump or a patient monitor. Why does cybersecurity matter?” Well, if you’re vulnerable, hackers can land a virus or Trojan software in your device; and, if your device contains a patient’s medical record number, for instance, they can then get into another one of the hospital’s information systems and launch an attack that way. So you’re part of the problem; you’re a potential weakness in the hospital.
Fernando: In product development, it used to be that your engineers would write all of the code that went into your device; but, as the development cycles needed to become more rapid and development processes became more agile, software engineers began taking advantage of open-sourced software in libraries, so software engineering, today, is like putting together a bunch of building blocks. The downside is that engineers don’t necessarily think a whole lot about pulling these library components in—it becomes almost second nature—and what happens is that you might not be aware of the vulnerabilities of those components. And sometimes, if you don’t keep track of your software materials as a developer, you may not even know what components were pulled in during the development process. As a result, we’ve seen statistics showing, for instance, that 90% of vulnerabilities seen in software-based products are a function of third-party libraries and open-sourced software [4].
IEEE Pulse: UL worked with the previous White House administration and met with government agencies and a wide range of industry leaders to come up with a UL cybersecurity certification for devices in 2016 that’s similar to the UL listing for electricity. How does this certification help?
Fernando: We developed the UL 2900 series of standards to serve across industries, including health care, to create, through repeatable and reproducible testing, objective evidence that manufacturers of these products have done their due diligence in identifying vulnerabilities [5]. This includes checking their products for malware; analyzing their source code for weaknesses; and doing what’s called fear, uncertainty, and doubt testing to try to identify new exploits that people might find.
Like other UL standards, the cybersecurity standards are almost exclusively voluntary consensus standards, which means that they provide value. The FDA recognizes the standards (as of August 2017), so medical device manufacturers can now use them to help get their devices through the regulatory process, because the FDA knows the developers have gone through the right set of requirements.
IEEE Pulse: What are Ivenix and Virta Labs doing on the cybersecurity front?
Gray: We are developing a new type of infusion pump and an infusion management system that is very information savvy and connected as a way to help reduce a lot of errors. [The Ivenix Infusion System is still 510(k) pending and is not commercially available in the United States at this time.] In fact, there are approximately 1.5 million adverse drug events a year, of which infusion-related errors are associated with just [more than] half [6], [7].
So, we built this new type of a system, architected as a computer with a back-end cloud in the hospital, that helps the infusion pumps talk to one another and learn. Given all of that, you can see that we are talking about connectivity, information, and sharing data about patients; so we started out with the understanding that the system must be very secure.
[To do that,] whether it’s the pump or the back-end system, we monitor for attacks. We have firewalls in multiple areas, so it’s hard to get through; and, even if you get through the first firewall, there’s another one. We encrypt all of our communications using https (a secure information-sharing or web-communications protocol), and we only communicate using https. In addition, our pump initiates all communication. That’s important because any device, like any website, can be overwhelmed by someone sending in a malicious barrage of communications, which can be repetitive information requests or even just saying “hi” over and over again, so we put security in place such that the pump can tell it’s talking to an Ivenix server, and, at the same time, the server through that connection can tell that it’s talking to an Ivenix pump.
Besides, of course, encrypting all of the data, we also give the hospital the ability to press a button and essentially reset the pump at any point in time. And when I say reset the pump, I don’t mean restart it; I mean wipe out all of the software, download an update of the software, and, in that process, wipe off any viruses and Trojans that might be there because of a breach.
Fu: Virta Labs produces BlueFlow, a software product for hospitals to help manage the risks of their medical devices and also to protect their clinical networks. It helps hospitals visualize that risk. Here’s a classic example: a report from the FBI warns about a particular virus or ransomware that affects a certain device, and the hospital has to know within a couple of minutes which devices it needs to secure or which devices to patch. Today, it’s very difficult, because you’d be surprised how many hospitals don’t have a handle on the medical-device inventory in their clinical networks, so, they run around like chickens with their heads cut off—definitely not a very healthy workflow.
Virta Labs helps with that by doing a full assessment of the inventory from a network perspective. Clinical IT staff needs to know every patch level of every machine and every medical device to make decisions. After all, you can’t triage until you know your risk. In essence, hospitals need the evidence-based assurance of availability of medical devices to deliver patient care despite computer-security risks.
IEEE Pulse: And Dr. Fu, what is your University of Michigan research group doing in terms of cybersecurity?
Fu: On the research front, we specialize in understanding how to prevent sensors from being tricked into delivering false data to a medical device that is making autonomous decisions (see photo at top). Here, we work on the security of sensors all the way from materials up through the operating system. The idea with this kind of work is to try to be a couple of steps ahead of the bad guys, and what we’re learning is that there do not appear to be adequate design controls in place to stop an adversary from controlling the output of the sensors.
For instance, we discovered that it’s quite easy to trick sensors into delivering false data by sending out malicious radio waves and malicious sound waves (below). And we demonstrated how a YouTube video containing music can be played on a particular smartphone and take control of the smartphone’s accelerometer, because it actually resonates material [8]. It’s physics: these sound waves bubble up in the operating system, causing the operating system to make incorrect decisions.
Overall, we’re looking at risks that frontline staff wouldn’t worry about too much today. But that in 10 years, [there] could very well be significant problems in medicine, such as pacemakers that make decisions on rate-adaptive pacing depending on a sensor, [and could also] extend outside medicine to things like autonomous vehicles that make kinetic decisions based on sensor data, or Internet-of-Things devices that change their settings depending on sensors. That’s why we’re very concerned about having the technology in place to protect the integrity of sensors.
IEEE Pulse: What advice do you have for developers to keep their medical devices secure?
Gray: They should start by going to some training [emphasizing] cybersecurity. Like everyone I know who has gone through it, including myself, when you come back from that week or two of training, you’re really nervous because you hear about all sorts of ways that [hackers] can get at you. Then, you need to start right at the beginning to understand your vulnerabilities and figure out how you can build in mitigations to security threats as you’re developing your system. I’ve been in the business of security for a long time, and I know that it’s really hard to do this after your product is already in the hands of customers.
[As development proceeds,] you also have to put in place the right organizational processes to respond to threats quickly. It’s not uncommon that a company in the medical industry will hear that it has a cyberthreat and either respond slowly or not at all. You just can’t do that anymore. You have to be prepared to move quickly.
Fernando: Just as I mentioned earlier, new technologies will have more and more interoperability moving forward, where devices can be connected in new ways and provide novel therapies and so on. We are seeing things like big data analytics, clinical-decision support, machine learning, artificial intelligence, and augmented reality—all of these are data-centric technology areas where we’ll inevitably see cybersecurity threats and expanding attack vectors. These new devices carry a lot of potential, but, to see that full potential, we will need to get past issues of cybersecurity, and the UL cybersecurity standards can help with that.
Bolting on cybersecurity measures after the fact is much more troublesome than baking it in from the start, so the best way to deploy security is to build it into the product right from concept through architecture and design cycles, and then implementation.
Fu: I think the main message is this: cybersecurity risks come with the territory. If you’re going to use a computer and have connectivity, then you’re unfortunately going to have real security risks, and you have to think about how to manage and mitigate those risks.
References:
- Virta Labs. (2017, Dec. 18). [Online].
- Ivenix Infusion Innovation. (2017, Dec. 18). [Online].
- J. Vijayan. (2014, Feb. 7). Target attack shows danger of remotely accessible HVAC systems: Qualys says about 55,000 Internet-connected heating systems, including one at the Sochi Olympic arena, lack adequate security. ComputerWorld. [Online].
- J. Corman, “DevOps will save the world: Public safety, public policy, and DevOps,” presented at the DevOps Enterprise Summit, San Francisco, CA, Oct. 2014.
- UL. (2016). Cybersecurity of medical devices and UL 2900. UL, Northbrook, IL. White Paper. [Online].
- U.S. Food and Drug Administration. (2017, May 8). Safe use initiative. [Online].
- R. Kaushal, D. W. Bates, C. Landrigan, K. J. McKenna, M. D. Clapp, F. Federico, and D. A. Goldmann, “Medication errors and adverse drug events in pediatric inpatients,” J. Amer. Medical Assoc., vol. 285, no. 16, pp. 2114–2120, Apr. 2001.
- T. Trippel, O. Weisse, W. Xu, P. Honeyman, and K. Fu, “WALNUT: Waging doubt on the integrity of MEMS accelerometers with acoustic injection attacks,” presented at the IEEE European Symp. Security and Privacy, Paris, France, Apr. 2017.



